Although a proxy by itself is not a virus, it can be used in conjunction with malware or as part of nefarious behavior. Proxy servers serve as a bridge between a company’s network and the internet.
A proxy virus can take control of the proxy server and function as a proxy bot if it infects a host machine that is connected to it. These bots can be used by attackers to launch anonymous network attacks. In this article, we aim to provide people with a clear understanding of how proxies fit into the larger picture of cybersecurity.

Is It Possible to Be Infected With Virus Through a Proxy?
Indeed, a virus can be a proxy. Malware that poses as a trustworthy proxy server is known as a proxy virus. A proxy virus that affects a user’s computer modifies the proxy settings to force all of the user’s internet traffic through the virus’s infected proxy server.
This enables the attacker to keep an eye on and eavesdrop on the victim’s online activity, steal private data, or direct the victim to dangerous websites. Several channels, including phishing emails, malicious attachments, and drive-by downloads, can be used to distribute proxy viruses.
Finding and getting rid of a proxy virus might be challenging once it has infected a user’s machine. This is because proxy viruses frequently alter the computer’s registry and system settings, making them challenging to remove. Some of the major dangers of proxy viruses are listed below.
Data Theft
Users’ passwords, credit card numbers, and other private information can be stolen through proxy viruses. The use of this information to commit fraud, identity theft, and other crimes is then possible.
Malware Infection
Trojans, spyware, and ransomware are just a few examples of malware that can be downloaded and installed on a user’s computer using proxy viruses. Trojans and spyware can grant remote access to the user’s computer, while ransomware can encrypt the user’s files and demand a ransom in exchange for the decryption key.
Internet Censorship
Proxy viruses can be used to deny users access to particular websites or to reroute them to harmful websites. By tricking users into downloading malware or disclosing sensitive information, this can be used to block users from accessing information.
Network Attacks
Attacks on other computers and networks can be launched using proxy malware. For instance, proxy viruses can be used to perform denial-of-service attacks, which can flood a network or website with traffic and prevent legitimate users from accessing it.
Man-in-the-middle attacks, which let attackers intercept and change communications between two parties, can also be launched using proxy infections. This can be used to propagate malware or steal confidential information.
Additional Dangers
Proxy infections can also result in additional issues, such as slower internet speeds, computer freezes or crashes, and difficulty accessing particular websites or online services, in addition to the risks already listed.
Virus Proxy Reports
Many websites exist that can evaluate proxy malware. Here are a few examples given below.
- VirusTotal
- ProxyScan
- ProxyChecker
- ProxyInspector
- IP Quality Score
Numerous antivirus software applications can check for proxy viruses in addition to these websites. Several instances include-
- Norton Antivirus
- McAfee Antivirus
- Bitdefender Antivirus
- ESET Antivirus
- Kaspersky Antivirus
Firewall Analyzer
Syslogs from proxy servers are frequently gathered by Firewall Analyzer. A built-in parser in its internal log processing engine allows it to recognize proxy infections for specific suppliers. Two different sorts of reports are produced by the Firewall Analyzer:
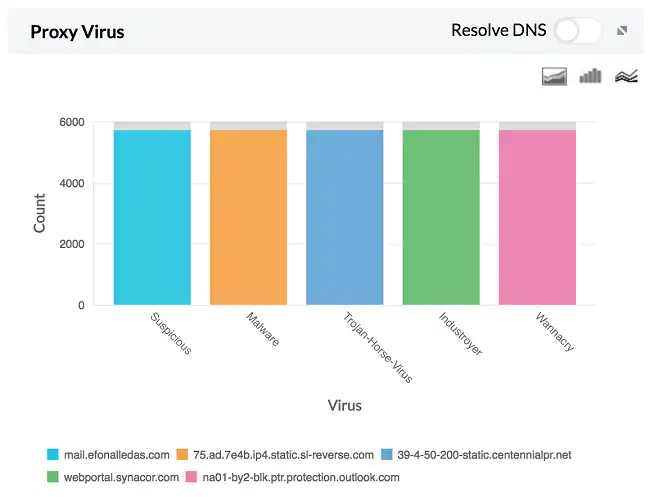
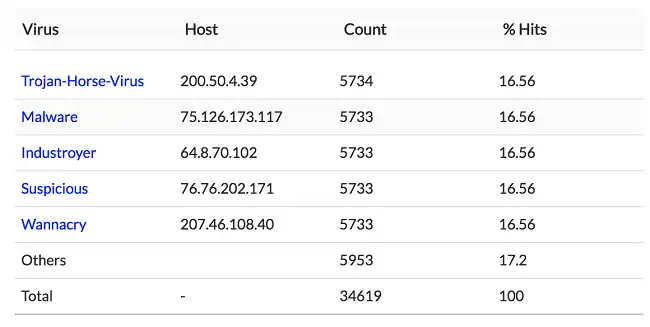
To see a detailed view of the host IP, destination IP, status, protocol, and time data, drill down on either of these reports.

Security administrators can identify and prevent harmful proxy virus hosts in each proxy server after analyzing the data to do so. The contaminated IPs can be found by administrators, and they can make plans to clean up such devices.
Frequently Asked Questions
How Do Proxy Virus Propagate?
Several channels, including phishing emails, malicious attachments, and drive-by downloads, can be used to distribute proxy viruses. Emails that are intended to deceive the recipient into clicking on a harmful link or opening a harmful attachment are known as phishing emails.
What Should I Do if I Think a Proxy Virus Has Attacked My Computer?
Run a complete system scan with a reliable antivirus program if you think your machine has a proxy virus. Additionally, you want to switch your proxy settings to manual and type in the IP address of a well-known and reliable proxy server.
How Can I Guard Against Proxy Viruses?
Be cautious while downloading attachments from emails and when opening emails. Update your antivirus program, and perform routine system scans. To prevent unauthorized access to your computer, use a firewall. Take caution while deciding which websites to visit and which links to click. Download software only from reliable sources.
Conclusion
One kind of malware known as proxy viruses can seriously endanger the security of your computer and the internet. They can be quite harmful and invade your cyber security. Our thorough coverage of the subject is intended to assist you in avoiding the risks.